Stage 1
first steps in this process is to analyze the image’s metadata. Metadata can contain valuable information such as the image’s creation date, camera settings, or even location data. By carefully inspecting this metadata, we might uncover useful details that can assist in solving the CTF challenge.
In this step, we use the ExifTool to extract metadata from the image.
exiftool ctf.jpg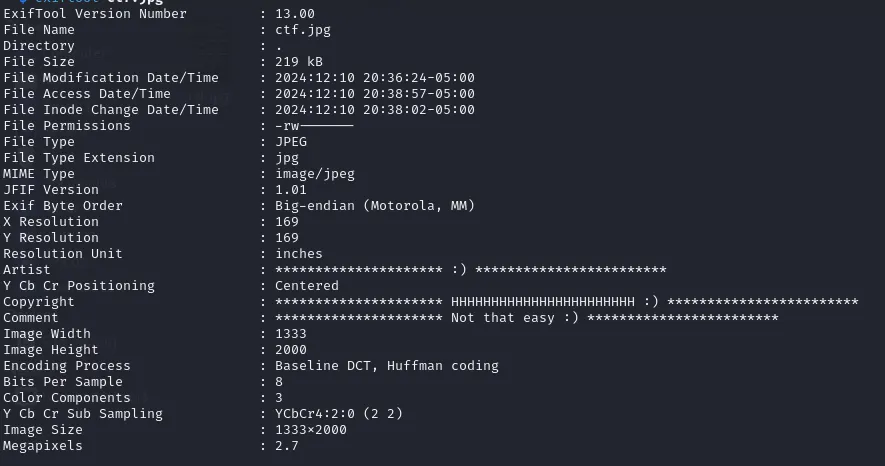
After we have extracted the metadata using ExifTool and could not find any evidence, we move on to searching for hidden files inside the file using Steghide. This tool is used to extract hidden data in images or other files.
$ steghide extract -sf ctf.jpg
Enter passphrase:
wrote extracted data to "secret.zip".$ unzip secret.zip
Archive: secret.zip
creating: secret/
extracting: secret/password is incorrect
inflating: secret/secret message
inflating: secret/stage2Ok, if we find three hidden files, the next step will be to analyze those files to discover their contents.
$ cat password\ is\ incorrect$ cat secret\ message
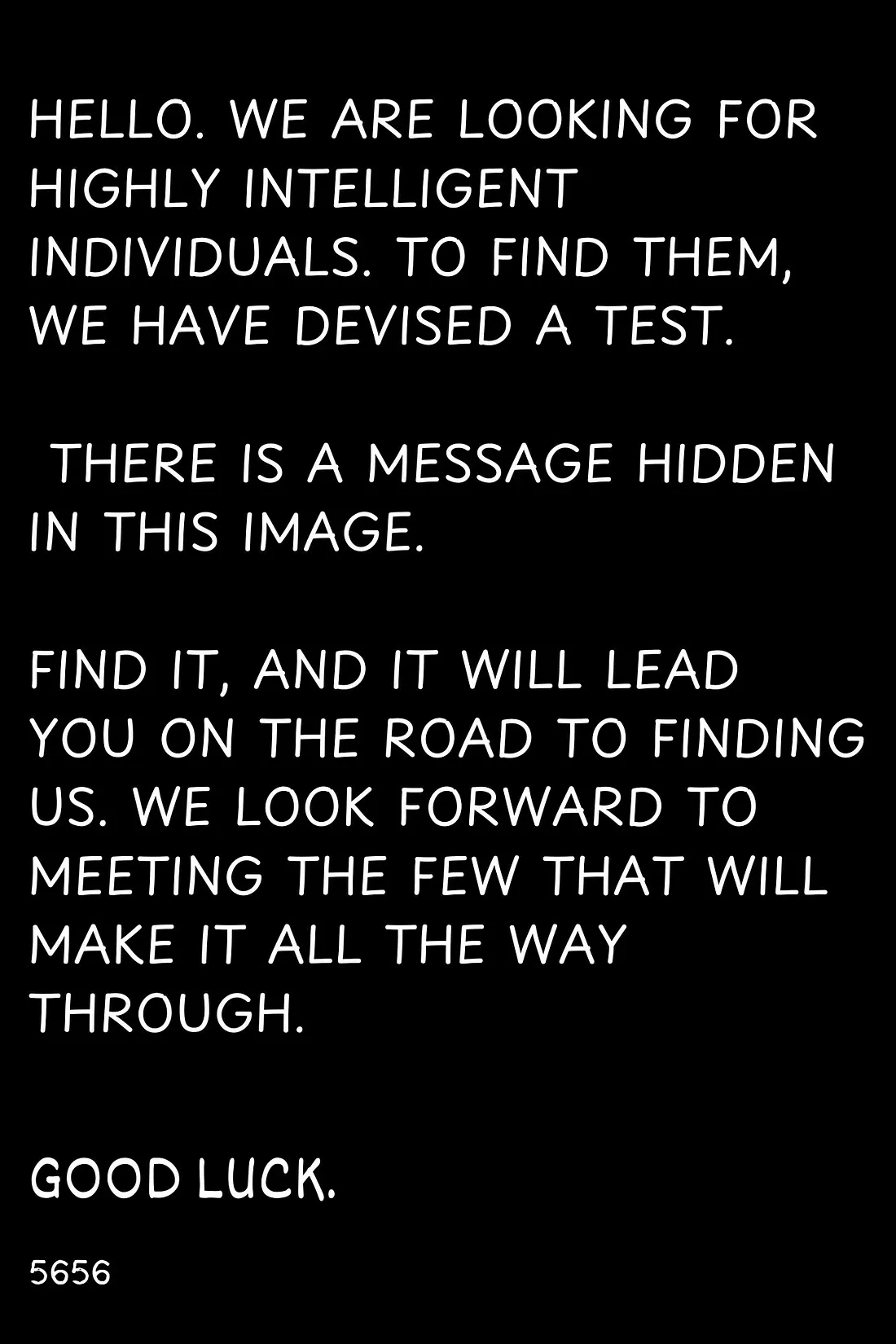
Well done reaching this stage, but this is only the beginning. The path ahead is longer and more mysterious than you can imagine. Your reward awaits, but the real trials have yet to begin... Prepare yourself.
Reward: c2VjdXJpbmV
Important note: The flag is divided into four parts, and you have now uncovered the first. The rest remain hidden, awaiting your discovery.Stage 2
$ cat stage2
Pbatenghyngvbaf ba fhpprffshyyl pbzcyrgvat lbhe frpbaq punyyratr. Jvgu gjb npuvrirzragf frpherq, lbh'er abj unysjnl guebhtu lbhe wbhearl. Jung yvrf nurnq erznvaf n zlfgrel, ohg jvgu rnpu fgrc, lbh rqtr pybfre gb znfgrevat gur haxabja. Fgnl funec, fgnl sbphfrq—terngre grfgf njnvg.
Frpbaq Njneq : 0p3fmozEsZT
Gur guveq gnfx: uggcf://zrtn.am/svyr/HkVtFEwP#RXcTpvjRIhNqvS5RC5rifSVeQd38IAkHCKO5BvYu2WbNow that we have the first reward and know that the flag is divided into four parts, we need to collect these parts to get the final flag.
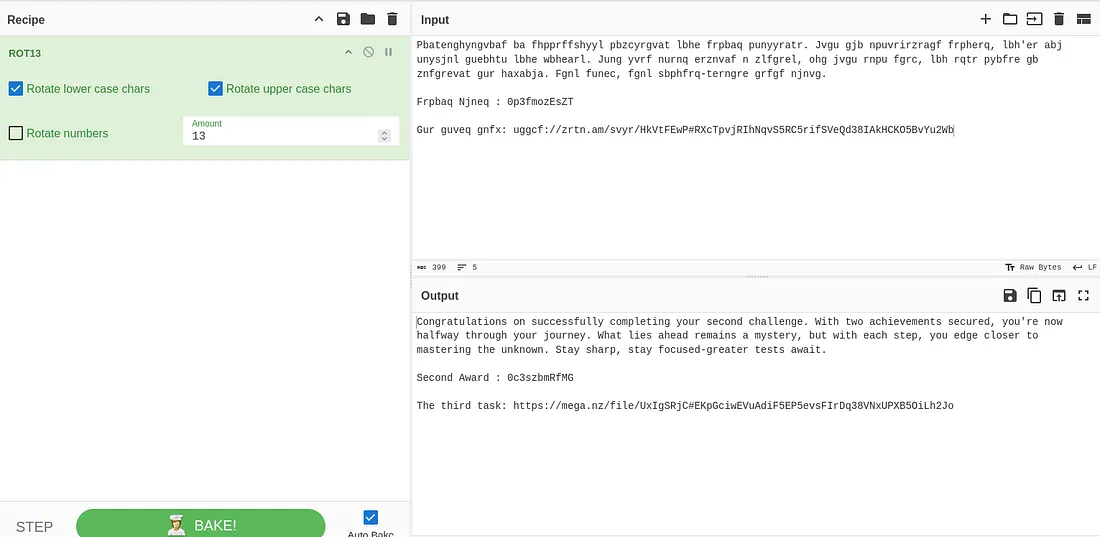
Excellent! Since the text is encrypted using ROT13 cipher, we can easily decrypt it.
Excellent! Since the second reward contains a link, the next step is to visit the link and check its contents. The link may contain more clues or may lead to a new stage in the challenge.
Stage 3
Great! Now that we have a new ZIP file from the link, the next step is to extract its contents and analyze them for more clues or information that might lead us to the flag.
$ unzip secret2.zip
Archive: secret2.zip
creating: secret2/
extracting: secret2/stage_4.zip
inflating: secret2/hintcat hint
In cybersecurity, gathering information is crucial, but the ability to exploit it is what sets the experts apart. Will you be one of them?
Your task: identify the car model associated with license plate "6656TU195".
Hint: The car model is the password that will grant you access to the fourth stage.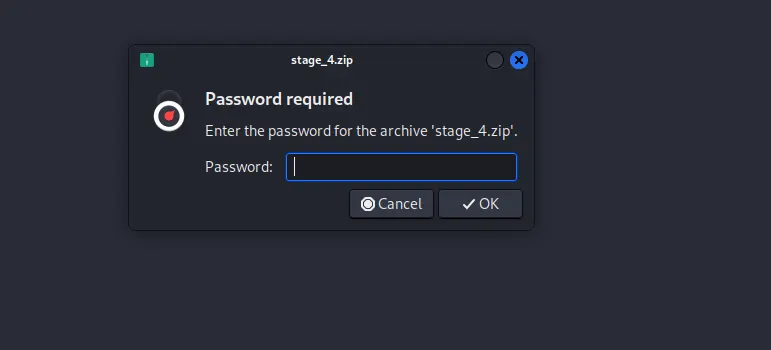
Since the secret2 file requires a password to unzip it and the password is linked to the license plate number 6656TU195, here are the steps you can follow:
If you had to use the https://vidange.tn/ website to get information about the car, the next step would be to visit the website and search for details about the car using the plate number 6656TU195
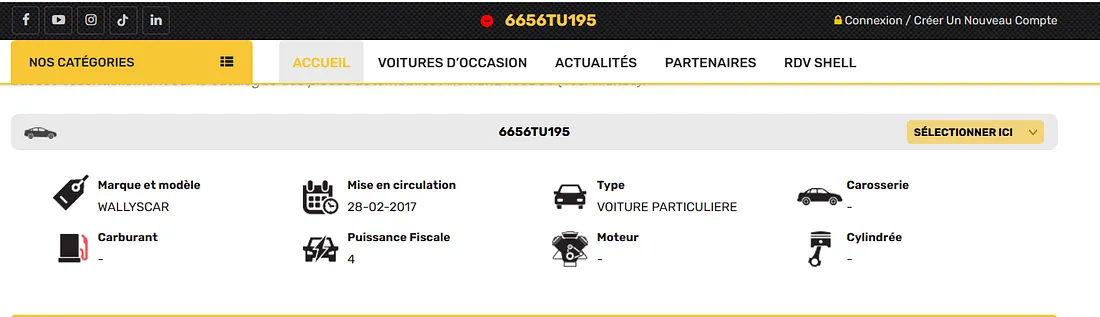
Great! Now that we have the WALLYSCAR password, you can use it to successfully decompress the file.
$ cat flag\ 3
Congratulations on making it this far. You're closer than ever, but the final challenge still awaits. Only by completing it can you secure your place among the few. Are you prepared for what comes next?
Reward: ZfdGgzXzRkdStage 4
cat stage\ 4
Success in the world of professional hacking hinges on a carefully crafted strategy; randomness has no place in your approach. Your next challenge is to decode this sentence, but be forewarned: it won't be an easy task.
" Zryoiu: jNudHVyM30 "
hint 1: Encryption name V * * * * * * e
hint 2: first stageWe have received the third reward, and to get the fourth reward we must decrypt this sentence. We notice that we have been given two hints to help us decrypt the cipher. From these two hints, we conclude that we must use the Vigenère Cipher to decrypt, and that the key to decrypt the cipher is in the first level.
Great! Since you noticed a file named “password is incorrect” at the first level, you can deduce that the key to decrypt is “incorrect”. Now that you have the key, you can use it to decrypt using the Vigenère Cipher.
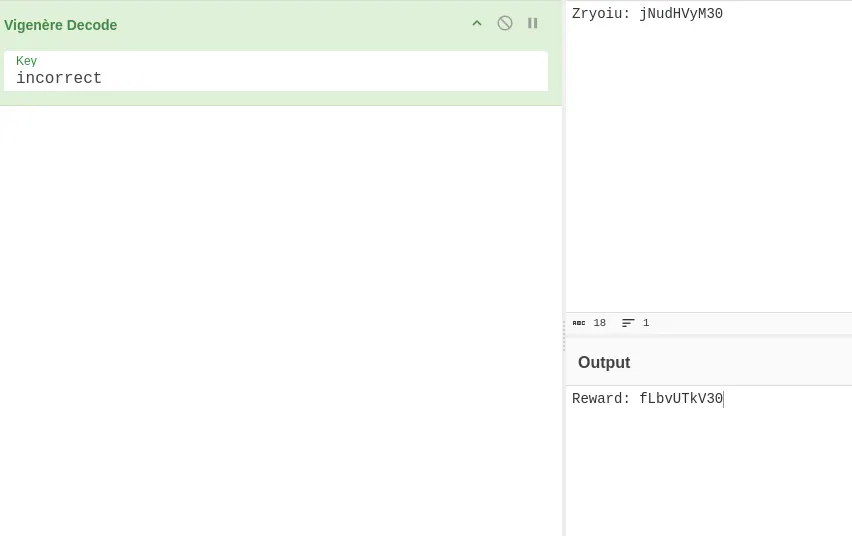
Great! We’ve decoded the sentence, and now we’ve got the fourth reward. Now we can get the final Flag.
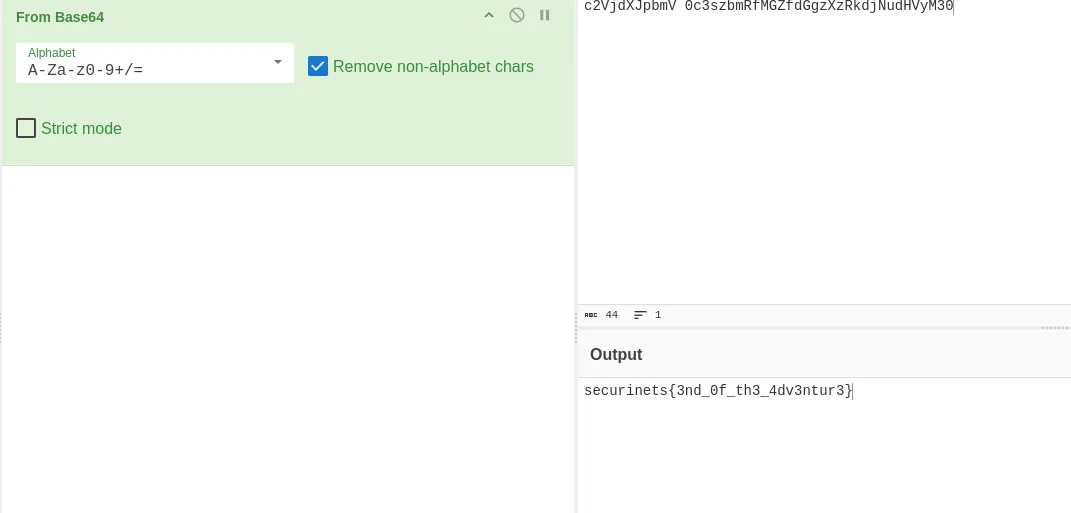
Congratulations! You have successfully completed the journey, and here is the final flag:
securinets{3nd_0f_th3_4dv3ntur3}